What Is a Firewall and How Can a VPN Bypass It? 2024
Firewalls are a type of security system that regulates the flow of network traffic coming into and going out of a network based on a set of established security rules.
Through the use of tunneling methods, obfuscating VPN traffic, encrypting data, or altering communication ports, a Virtual Private Network (VPN) is able to circumvent some firewalls.
On the other hand, it is not possible to circumvent every firewall, particularly those that take advantage of sophisticated deep packet inspection methods.
We Recommend Nord VPN as we have tested this Firewall and it does its job perfectly. You can take a free trial from the below link only.
A firewall is a security system that monitors network traffic based on security rules. The main purpose of a firewall is to protect a network and its resources from unauthorized access and malicious traffic. Firewalls can be software-based or hardware-based and are commonly used by organizations of all sizes to secure their networks.
What is a firewall?
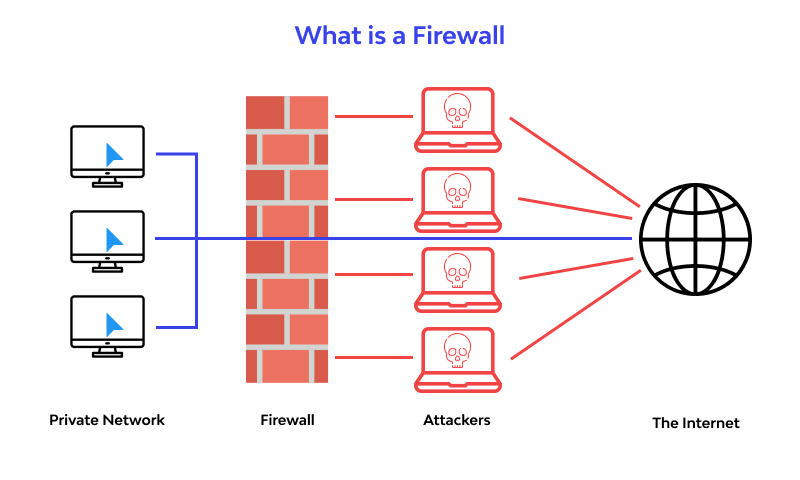
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. A firewall can be implemented as a software application, a hardware appliance, or a combination of both. Firewalls are commonly used by organizations of all sizes to protect their networks from unauthorized access and malicious traffic.
The primary function of a firewall is to control the flow of network traffic based on predetermined security rules. For example, a firewall might allow incoming and outgoing traffic only for specific IP addresses, ports, and protocols.
Firewalls can be configured to operate at different levels of the network, including the application layer, transport layer, and network layer. Firewalls that operate at the application layer are often referred to as application firewalls and can provide more granular control over network traffic.
How does a firewall work?
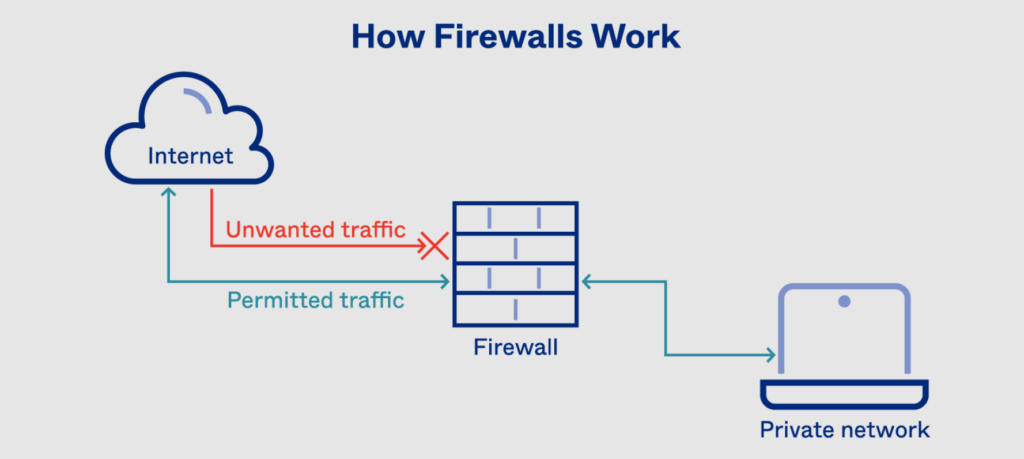
Firewalls operate by inspecting incoming and outgoing network traffic and applying predetermined security rules to that traffic. Firewalls can be configured to operate in a variety of ways, including stateful and stateless inspection.
Stateful inspection firewalls keep track of the state of network connections and only allow traffic that is part of an established connection. For example, a stateful inspection firewall might allow incoming traffic from a web server only if there is an established connection between the client and the server.
Stateless inspection firewalls examine each packet of network traffic individually and do not keep track of the state of network connections. Stateless inspection firewalls are less complex than stateful inspection firewalls and are often used in high-speed network environments.
Firewalls can also be configured to operate in different modes, including transparent mode and routed mode. In transparent mode, the firewall is placed between two network segments and operates as a bridge, while in routed mode, the firewall acts as a router and routes traffic between different network segments.
Why do you need a firewall?
Firewalls are essential for securing networks and protecting sensitive information from unauthorized access and malicious traffic. Without a firewall, networks are vulnerable to attacks such as viruses, malware, and hacking attempts.
Firewalls provide a layer of security between a network and the internet, controlling the flow of traffic and enforcing security policies. Additionally, firewalls can be configured to log network traffic, providing an audit trail that can be used for forensic analysis in the event of a security breach.
How does a VPN work?
A VPN (Virtual Private Network) is a technology that creates a secure and encrypted connection between a user’s device and the internet. VPNs are commonly used to protect a user’s online privacy and security by masking their IP address and encrypting their internet traffic.
When a user connects to a VPN server, their internet traffic is routed through the VPN server before reaching the internet. This provides several benefits, including:
Encryption: VPNs encrypt all internet traffic, making it unreadable to anyone who intercepts it.
Can VPNs be blocked by the government?
Yes, VPNs can easily be blocked by the government. They have control over VPN ports, VPN provider lists, protocols, etc., and they can even blacklist VPN IPs as well.
They have experts to monitor VPN activities, so they don’t create a country’s threat while using VPN services.
IP address masking
#1. IP address masking: VPNs mask a user’s IP address, making it difficult for websites and online services to track their online activity and location.
#2. Access to restricted content: VPNs allow users to access online content that may be restricted in their location or region, such as streaming services or social media platforms.
#3. Public Wi-Fi security: VPNs can provide added security when using public Wi-Fi networks, which are often unsecured and vulnerable to hacking attempts.
How Can a VPN Bypass a Firewall or ISP Firewall?
In some cases, a firewall may block a VPN connection, preventing users from accessing the internet via the VPN. This can be due to several reasons, such as the firewall blocking the VPN protocol or the VPN server being on a blacklist.
However, there are several ways that a VPN can bypass a firewall, including:
Using a different VPN protocol: Some firewalls may block specific VPN protocols, such as PPTP or L2TP. Switching to a different VPN protocol, such as OpenVPN, may allow the VPN connection to bypass the firewall.
#1. Changing the VPN port: VPN traffic typically uses specific ports, such as port 1194 for OpenVPN. Some firewalls may block these ports, preventing the VPN connection from establishing itself. Changing the VPN port to a less commonly blocked port, such as port 443 (used for HTTPS traffic), may allow the VPN connection to bypass the firewall.
#2. Using stealth VPN technology: stealth VPN technology is designed to make VPN traffic appear as regular HTTPS traffic, making it difficult for firewalls to detect and block the VPN connection. Stealth VPN technology is often used in countries with strict internet censorship, such as China and Iran.
#3. Using a dedicated IP address: Some VPN providers offer dedicated IP addresses that are not shared with other users. This can make it more difficult for firewalls to detect and block the VPN connection, as the IP address is not associated with a known VPN server.
#4. Using a VPN server in a different location: Some firewalls may block VPN connections to specific VPN servers or locations. Using a VPN server in a different location, such as a different country, may allow the VPN connection to bypass the firewall.
It is important to note that bypassing a firewall using a VPN may not always be legal or ethical. In some cases, governments and organizations may have legitimate reasons for blocking certain types of internet traffic, and attempting to bypass these restrictions may be illegal. Additionally, some websites and online services may have terms of service agreements that prohibit the use of VPNs to access their content.
Conclusion
In conclusion, firewalls are essential for securing networks and protecting sensitive information from unauthorized access and malicious traffic. Firewalls can be configured to operate in a variety of ways, including stateful and stateless inspection, and can be placed in different modes, including transparent mode and routed mode.
VPNs are a technology that creates a secure and encrypted connection between a user’s device and the internet, providing several benefits, including encryption, IP address masking, access to restricted content, and public Wi-Fi security. In some cases, a firewall may block a VPN connection, preventing users from accessing the internet via the VPN.
However, there are several ways that a VPN can bypass a firewall, including using a different VPN protocol, changing the VPN port, using stealth VPN technology, using a dedicated IP address, and using a VPN server in a different location. It is important to note that attempting to bypass a firewall using a VPN may not always be legal or ethical, and users should carefully consider the implications before attempting to do so.
I'm a technology cyber expert and VPN expert. I love to stay up-to-date on the latest tech trends and explore new ways to use technology to improve my life. I also enjoy writing about these topics.
Peace ✌️


